前書き
さて、今回はFlexVPNを構築してみました。
私はCiscoは初心者過ぎて、DMVPNでないとHUB-SPOKEのIPsecを張れないと思ってました。
できるんだなこれが。
FlexVPNとは何ぞという方に簡単に説明するとVirtual-Templateのトンネルタイプを使った設定簡易なIPsec接続のことだと思っています。
そもそも1対N(Point-to-MultiPoint)であるHUB-SPOKEと1対1(Point-to-Point)であるIPsecはすこぶる相性が悪く、IPsecでカプセル化せずにPoint-to-MultiPointに対応したmGREを使おうというのがDMVPNの考え方です。これによって、SPOKEが増えた際にもHUB側のコンフィグレーションをいじらなくてよい環境が出来上がります。
割と昔からあるらしいVirtual-Templeteという機能を使うことで論理インタフェースの自動生成が可能であり、Point-to-PointのIPsecでも同じことが実現可能です。これをdVTIを使ったFlexVPNと呼んでいます。
じゃあどっち使えばいいのかですが、基本的にはFlexVPNの方が後継のためこちらを使うことになります。
DMVPNではIKEv2ができないと記載されているサイトなども見ましたが、どうやらできるようですし、DMVPNとFlexVPNの違いは何かと言われると、自分もこれといった回答は持っていないです。
少なくともDMVPNはmGREが必須なのでPoint-to-MultiPointになりますが、FlexVPNではmGREを使えばPoint-to-MultiPointもできますし、dVTIを使えばPoint-to-Point構成も可能です。
あとは、mGREを使っている以上IPsecのトランスポートモードを使ったとしても、VTIのIPsecトンネルモードだけの状態に比べて4bitほどMTUが多く必要なくらいでしょうか。
環境
CMLをProxmoxVE上に立てて環境構築しました。
- CML2.7
次に各ノードの紹介です。
Catalyst 8000v ×4(以降cat8000v)
IOSv ×1(以降iosv)
構成図
今回はこんな感じです。
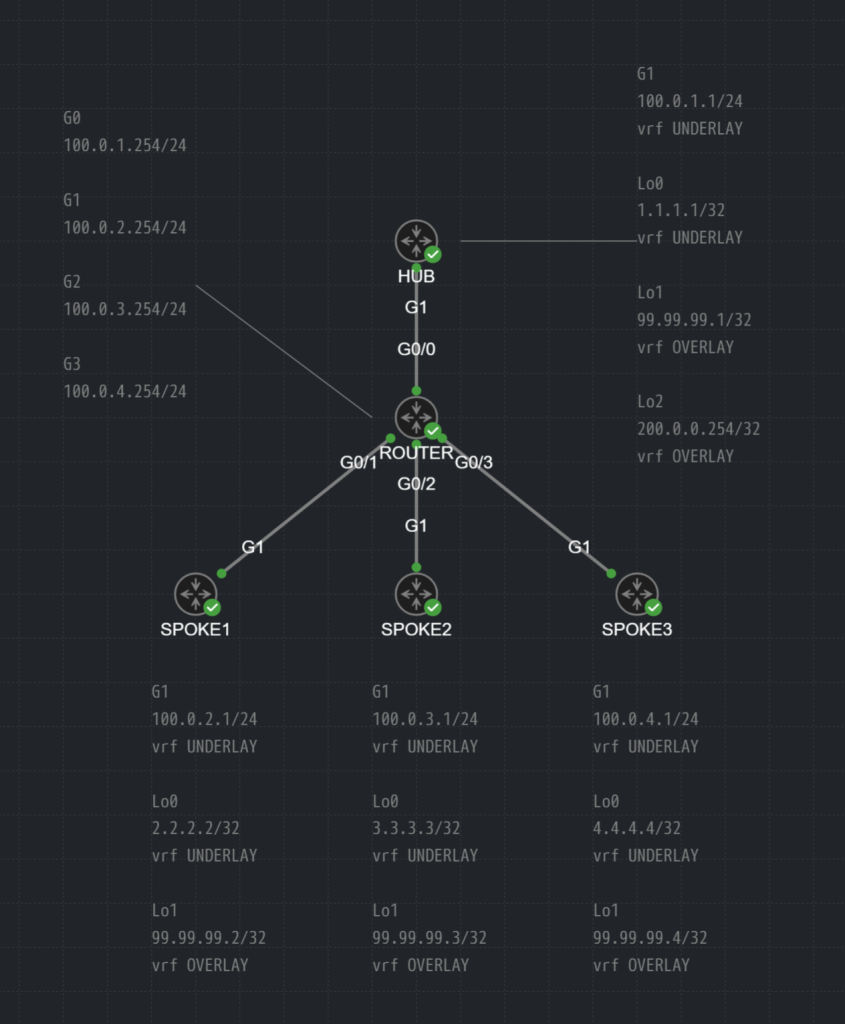
図でうまく表現できなかったのでサボりましたが、ルーティングプロトコルは以下の構成です。
アンダーレイ:IS-IS レベル1
オーバーレイ:OSPF エリア0
実はFlexVPNではオーバーレイにEIGRPやBGPを使うことが推奨されており、OSPFで構築している例はどこにも載ってません。これが稚拙をインターネットに残す理由の一つです。
今回はIPsecにもこだわっており、AES-GCM-265でPFSのフル装備です。コンフィグが長くなっている原因の半分は多分このこだわりのせいです🙄
また、ついでにFVRF(Front door VRF)もつけてみました、簡単に言うとアンダーレイとオーバーレイのルーティング分離ですね。
FlexVPNでFVRFをしている例もCiscoのドキュメントにはほとんどありません。
この機能のおかげでオーバーレイにいるユーザにアンダーレイのネットワークへの到達ができない状況を構築可能です。多分回線事業者がWANとかに使ってるんですかね。知らんけど。
今回の目玉はまとめるとこんな感じでしょうか。
- OSPF over FlexVPN
- FVRF
- つよつよIPsec🙄
コンフィグ
予め、cat8000vの4台はライセンスのアドバンテージライセンス有効化済みの前提です。
HUB
en
!
conf t
!
hostname HUB
!
ip local pool SPOKE_TUNNEL_IP 200.0.0.1 200.0.0.10 →SPOKEのトンネルIFに自動で振るIPのレンジ
!
ip vrf UNDERLAY
rd 65001:1
!
ip vrf OVERLAY
rd 65001:2
!
interface GigabitEthernet1
ip vrf forwarding UNDERLAY
ip address 100.0.1.1 255.255.255.0
ip router isis tagUNDERLAY →IS-ISタグ名です。IS-ISはタグ名とVRFが1対1で紐づけられます。
no shutdown
!
interface Loopback0
ip vrf forwarding UNDERLAY
ip address 1.1.1.1 255.255.255.255
ip router isis tagUNDERLAY
!
interface Loopback1
ip vrf forwarding OVERLAY
ip address 99.99.99.1 255.255.255.255
ip ospf 1 area 0
!
interface Loopback2
ip vrf forwarding OVERLAY
ip address 200.0.0.254 255.255.255.255
!
crypto ikev2 proposal IKE_PROPOSAL
encryption aes-gcm-256 →諸悪の根源です。
prf sha512 →aes-gcmでは必須の設定です。integrity sha512ではNGです。
group 19
!
crypto ikev2 policy IKE_POLLICY
match fvrf UNDERLAY →VRFありではこれがないとIKEネゴしてくれません。
proposal IKE_PROPOSAL
!
crypto ikev2 authorization policy default
pool SPOKE_TUNNEL_IP
route set interface →Virtual-Templateの経路をスタティックで自動設定してくれます。
!
crypto ikev2 keyring KEY_RING
peer spoke
address 0.0.0.0 0.0.0.0 →スポークが動的でなければIPは絞れます。
pre-shared-key Cisco
!
crypto ipsec transform-set TRANSFORM_SET esp-gcm →諸悪の根源です。
mode tunnel
!
crypto ikev2 profile IKE_PROFILE
match fvrf UNDERLAY →VRFありではこれがないとIKEネゴしてくれません。
match identity remote any →スポークが動的でなければIPは絞れます。
authentication remote pre-share
authentication local pre-share
aaa authorization group psk list default default →IKEの認証に必要らしいです。
keyring local KEY_RING
virtual-template 1 →後述のVirtual-Templateを紐づけます
dpd 30 6 on-demand →合計 66 秒(30 + 6 + 6 X 5 = 66)間ピアの応答がなければdownします。
lifetime 300 →ike saのライフタイムです。
!
crypto ipsec profile IPSEC_PROFILE
set transform-set TRANSFORM_SET
set ikev2-profile IKE_PROFILE
set pfs group19 →ipsecのPFSです。
set security-association lifetime seconds 900 →ipsec saのライフタイムです。900が最短です。
!
interface Virtual-Template1 type tunnel
ip vrf forwarding OVERLAY →FVRFに必須の設定です。
ip unnumbered Loopback2
ip nhrp network-id 1 →ショートカットVPNに必須です。
ip nhrp redirect →ショートカットVPNに必須です。
tunnel source GigabitEthernet1
tunnel protection ipsec profile IPSEC_PROFILE
tunnel vrf UNDERLAY →FVRFに必須の設定です。
ip ospf 1 area 0
!
router ospf 1 vrf OVERLAY
router-id 1.1.1.1
!
router isis tagUNDERLAY
net 49.0001.0010.0100.1001.00
is-type level-1
vrf UNDERLAY →IS-ISのVRF紐づけです。
!
end
!残りはコメントは省略します。
SPOKE1
en
!
conf t
!
hostname SPOKE1
!
ip vrf UNDERLAY
rd 65001:1
!
ip vrf OVERLAY
rd 65001:2
!
interface GigabitEthernet1
ip vrf forwarding UNDERLAY
ip address 100.0.2.1 255.255.255.0
ip router isis tagUNDERLAY
no shutdown
!
interface Loopback0
ip vrf forwarding UNDERLAY
ip address 2.2.2.2 255.255.255.255
ip router isis tagUNDERLAY
!
interface Loopback1
ip vrf forwarding OVERLAY
ip address 99.99.99.2 255.255.255.255
ip ospf 1 area 0
!
crypto ikev2 proposal IKE_PROPOSAL
encryption aes-gcm-256
prf sha512
group 19
!
crypto ikev2 policy IKE_POLLICY
match fvrf UNDERLAY
proposal IKE_PROPOSAL
!
crypto ikev2 authorization policy default
route set interface
!
crypto ikev2 keyring KEY_RING
peer hub
address 0.0.0.0 0.0.0.0
pre-shared-key Cisco
!
crypto ikev2 profile IKE_PROFILE
match fvrf UNDERLAY
match identity remote address 0.0.0.0
authentication remote pre-share
authentication local pre-share
keyring local KEY_RING
aaa authorization group psk list default default
virtual-template 1
dpd 30 6 on-demand
lifetime 300
!
crypto ipsec transform-set TRANSFORM_SET esp-gcm
mode tunnel
!
crypto ipsec profile IPSEC_PROFILE
set transform-set TRANSFORM_SET
set ikev2-profile IKE_PROFILE
set pfs group19
set security-association lifetime seconds 900
!
interface Virtual-Template1 type tunnel
ip vrf forwarding OVERLAY
ip unnumbered tunnel 0
ip nhrp network-id 1
ip nhrp shortcut virtual-template 1
ip nhrp redirect
tunnel source GigabitEthernet1
tunnel protection ipsec profile IPSEC_PROFILE
tunnel vrf UNDERLAY
ip ospf priority 0
ip ospf 1 area 0
!
interface tunnel 0
ip vrf forwarding OVERLAY
ip address negotiated
ip nhrp network-id 1
ip nhrp shortcut virtual-template 1
ip nhrp redirect
tunnel source GigabitEthernet1
tunnel destination 100.0.1.1
tunnel protection ipsec profile IPSEC_PROFILE
tunnel vrf UNDERLAY
ip ospf priority 0
ip ospf 1 area 0
!
crypto ikev2 client flexvpn FLEXVPN_CLIENT
peer 1 100.0.1.1
client connect Tunnel0
!
router ospf 1 vrf OVERLAY
router-id 2.2.2.2
!
router isis tagUNDERLAY
net 49.0001.0020.0200.2002.00
is-type level-1
vrf UNDERLAY
!
end
!SPOKE2
en
!conf t
!
hostname SPOKE2
!
ip vrf UNDERLAY
rd 65001:1
!
ip vrf OVERLAY
rd 65001:2
!
interface GigabitEthernet1
ip vrf forwarding UNDERLAY
ip address 100.0.3.1 255.255.255.0
ip router isis tagUNDERLAY
no shutdown
!
interface Loopback0
ip vrf forwarding UNDERLAY
ip address 3.3.3.3 255.255.255.255
ip router isis tagUNDERLAY
!
interface Loopback1
ip vrf forwarding OVERLAY
ip address 99.99.99.3 255.255.255.255
ip ospf 1 area 0
!
crypto ikev2 proposal IKE_PROPOSAL
encryption aes-gcm-256
prf sha512
group 19
!
crypto ikev2 policy IKE_POLLICY
match fvrf UNDERLAY
proposal IKE_PROPOSAL
!
crypto ikev2 authorization policy default
route set interface
!
crypto ikev2 keyring KEY_RING
peer hub
address 0.0.0.0 0.0.0.0
pre-shared-key Cisco
!
crypto ikev2 profile IKE_PROFILE
match fvrf UNDERLAY
match identity remote address 0.0.0.0
authentication remote pre-share
authentication local pre-share
keyring local KEY_RING
aaa authorization group psk list default default
virtual-template 1
dpd 30 6 on-demand
lifetime 300
!
crypto ipsec transform-set TRANSFORM_SET esp-gcm
mode tunnel
!
crypto ipsec profile IPSEC_PROFILE
set transform-set TRANSFORM_SET
set ikev2-profile IKE_PROFILE
set pfs group19
set security-association lifetime seconds 900
!
interface Virtual-Template1 type tunnel
ip vrf forwarding OVERLAY
ip unnumbered tunnel 0
ip nhrp network-id 1
ip nhrp shortcut virtual-template 1
ip nhrp redirect
tunnel source GigabitEthernet1
tunnel protection ipsec profile IPSEC_PROFILE
tunnel vrf UNDERLAY
ip ospf priority 0
ip ospf 1 area 0
!
interface tunnel 0
ip vrf forwarding OVERLAY
ip address negotiated
ip nhrp network-id 1
ip nhrp shortcut virtual-template 1
ip nhrp redirect
tunnel source GigabitEthernet1
tunnel destination 100.0.1.1
tunnel protection ipsec profile IPSEC_PROFILE
tunnel vrf UNDERLAY
ip ospf priority 0
ip ospf 1 area 0
!
crypto ikev2 client flexvpn FLEXVPN_CLIENT
peer 1 100.0.1.1
client connect Tunnel0
!
router ospf 1 vrf OVERLAY
router-id 3.3.3.3
!
router isis tagUNDERLAY
net 49.0001.0030.0300.3003.00
is-type level-1
vrf UNDERLAY
!
end
!SPOKE3
en
!
conf t
!
hostname SPOKE3
!
ip vrf UNDERLAY
rd 65001:1
!
ip vrf OVERLAY
rd 65001:2
!
interface GigabitEthernet1
ip vrf forwarding UNDERLAY
ip address 100.0.4.1 255.255.255.0
ip router isis tagUNDERLAY
no shutdown
!
interface Loopback0
ip vrf forwarding UNDERLAY
ip address 4.4.4.4 255.255.255.255
ip router isis tagUNDERLAY
!
interface Loopback1
ip vrf forwarding OVERLAY
ip address 99.99.99.4 255.255.255.255
ip ospf 1 area 0
!
crypto ikev2 proposal IKE_PROPOSAL
encryption aes-gcm-256
prf sha512
group 19
!
crypto ikev2 policy IKE_POLLICY
match fvrf UNDERLAY
proposal IKE_PROPOSAL
!
crypto ikev2 authorization policy default
route set interface
!
crypto ikev2 keyring KEY_RING
peer hub
address 0.0.0.0 0.0.0.0
pre-shared-key Cisco
!
crypto ikev2 profile IKE_PROFILE
match fvrf UNDERLAY
match identity remote address 0.0.0.0
authentication remote pre-share
authentication local pre-share
keyring local KEY_RING
aaa authorization group psk list default default
virtual-template 1
dpd 30 6 on-demand
lifetime 300
!
crypto ipsec transform-set TRANSFORM_SET esp-gcm
mode tunnel
!
crypto ipsec profile IPSEC_PROFILE
set transform-set TRANSFORM_SET
set ikev2-profile IKE_PROFILE
set pfs group19
set security-association lifetime seconds 900
!
interface Virtual-Template1 type tunnel
ip vrf forwarding OVERLAY
ip unnumbered tunnel 0
ip nhrp network-id 1
ip nhrp shortcut virtual-template 1
ip nhrp redirect
tunnel source GigabitEthernet1
tunnel protection ipsec profile IPSEC_PROFILE
tunnel vrf UNDERLAY
ip ospf priority 0
ip ospf 1 area 0
!
interface tunnel 0
ip vrf forwarding OVERLAY
ip address negotiated
ip nhrp network-id 1
ip nhrp shortcut virtual-template 1
ip nhrp redirect
tunnel source GigabitEthernet1
tunnel destination 100.0.1.1
tunnel protection ipsec profile IPSEC_PROFILE
tunnel vrf UNDERLAY
ip ospf priority 0
ip ospf 1 area 0
!
crypto ikev2 client flexvpn FLEXVPN_CLIENT
peer 1 100.0.1.1
client connect Tunnel0
!
router ospf 1 vrf OVERLAY
router-id 4.4.4.4
!
router isis tagUNDERLAY
net 49.0001.0040.0400.4004.00
is-type level-1
vrf UNDERLAY
!
end
!ROUTER
en
!
conf t
!
hostname ROUTER
!
interface GigabitEthernet0/0
ip address 100.0.1.254 255.255.255.0
ip router isis
no shutdown
!
interface GigabitEthernet0/1
ip address 100.0.2.254 255.255.255.0
ip router isis
no shutdown
!
interface GigabitEthernet0/2
ip address 100.0.3.254 255.255.255.0
ip router isis
no shutdown
!
interface GigabitEthernet0/3
ip address 100.0.4.254 255.255.255.0
ip router isis
no shutdown
!
interface Loopback0
ip address 50.50.50.50 255.255.255.255
ip router isis
!
router isis
net 49.0001.0500.5005.0050.00
is-type level-1
!
end
!showコマンド結果
show isis topology
HUB
HUB#show isis topology
Tag tagUNDERLAY:
IS-IS TID 0 paths to level-1 routers
System Id Metric Next-Hop Interface SNPA
HUB --
SPOKE1 20 ROUTER Gi1 5254.001a.3520
SPOKE2 20 ROUTER Gi1 5254.001a.3520
SPOKE3 20 ROUTER Gi1 5254.001a.3520
ROUTER 10 ROUTER Gi1 5254.001a.3520SPOKE1
SPOKE1#show isis topology
Tag tagUNDERLAY:
IS-IS TID 0 paths to level-1 routers
System Id Metric Next-Hop Interface SNPA
HUB 20 ROUTER Gi1 5254.0010.4ada
SPOKE1 --
SPOKE2 20 ROUTER Gi1 5254.0010.4ada
SPOKE3 20 ROUTER Gi1 5254.0010.4ada
ROUTER 10 ROUTER Gi1 5254.0010.4ada SPOKE2
SPOKE2#show isis topology
Tag tagUNDERLAY:
IS-IS TID 0 paths to level-1 routers
System Id Metric Next-Hop Interface SNPA
HUB 20 ROUTER Gi1 5254.0000.6ffd
SPOKE1 20 ROUTER Gi1 5254.0000.6ffd
SPOKE2 --
SPOKE3 20 ROUTER Gi1 5254.0000.6ffd
ROUTER 10 ROUTER Gi1 5254.0000.6ffdSPOKE3
SPOKE3#show isis topology
Tag tagUNDERLAY:
IS-IS TID 0 paths to level-1 routers
System Id Metric Next-Hop Interface SNPA
HUB 20 ROUTER Gi1 5254.0011.26f2
SPOKE1 20 ROUTER Gi1 5254.0011.26f2
SPOKE2 20 ROUTER Gi1 5254.0011.26f2
SPOKE3 --
ROUTER 10 ROUTER Gi1 5254.0011.26f2ROUTER
ROUTER#show isis topology
IS-IS TID 0 paths to level-1 routers
System Id Metric Next-Hop Interface SNPA
HUB 10 HUB Gi0/0 5254.0013.fe4b
SPOKE1 10 SPOKE1 Gi0/1 5254.000d.7f7e
SPOKE2 10 SPOKE2 Gi0/2 5254.001b.0ea3
SPOKE3 10 SPOKE3 Gi0/3 5254.001d.3078
ROUTER --show ip route
ROUTER
ROUTER#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
1.0.0.0/32 is subnetted, 1 subnets
i L1 1.1.1.1 [115/20] via 100.0.1.1, 01:28:18, GigabitEthernet0/0
2.0.0.0/32 is subnetted, 1 subnets
i L1 2.2.2.2 [115/20] via 100.0.2.1, 01:25:21, GigabitEthernet0/1
3.0.0.0/32 is subnetted, 1 subnets
i L1 3.3.3.3 [115/20] via 100.0.3.1, 02:05:17, GigabitEthernet0/2
4.0.0.0/32 is subnetted, 1 subnets
i L1 4.4.4.4 [115/20] via 100.0.4.1, 02:04:50, GigabitEthernet0/3
50.0.0.0/32 is subnetted, 1 subnets
C 50.50.50.50 is directly connected, Loopback0
100.0.0.0/8 is variably subnetted, 8 subnets, 2 masks
C 100.0.1.0/24 is directly connected, GigabitEthernet0/0
L 100.0.1.254/32 is directly connected, GigabitEthernet0/0
C 100.0.2.0/24 is directly connected, GigabitEthernet0/1
L 100.0.2.254/32 is directly connected, GigabitEthernet0/1
C 100.0.3.0/24 is directly connected, GigabitEthernet0/2
L 100.0.3.254/32 is directly connected, GigabitEthernet0/2
C 100.0.4.0/24 is directly connected, GigabitEthernet0/3
L 100.0.4.254/32 is directly connected, GigabitEthernet0/3show ip interface brief
HUB
HUB#show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet1 100.0.1.1 YES manual up up
GigabitEthernet2 unassigned YES NVRAM administratively down down
GigabitEthernet3 unassigned YES NVRAM administratively down down
GigabitEthernet4 unassigned YES NVRAM administratively down down
Loopback0 1.1.1.1 YES manual up up
Loopback1 99.99.99.1 YES manual up up
Loopback2 200.0.0.254 YES manual up up
Virtual-Access1 200.0.0.254 YES unset up up
Virtual-Access2 200.0.0.254 YES unset up up
Virtual-Access3 200.0.0.254 YES unset up up
Virtual-Template1 200.0.0.254 YES unset up downSPOKE1
SPOKE1#show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet1 100.0.2.1 YES manual up up
GigabitEthernet2 unassigned YES NVRAM administratively down down
GigabitEthernet3 unassigned YES NVRAM administratively down down
GigabitEthernet4 unassigned YES NVRAM administratively down down
Loopback0 2.2.2.2 YES manual up up
Loopback1 99.99.99.2 YES manual up up
Tunnel0 200.0.0.3 YES manual up up
Virtual-Access1 200.0.0.3 YES unset up up
Virtual-Access2 200.0.0.3 YES unset up up
Virtual-Template1 200.0.0.3 YES unset up downSPOKE2
SPOKE2#show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet1 100.0.3.1 YES manual up up
GigabitEthernet2 unassigned YES NVRAM administratively down down
GigabitEthernet3 unassigned YES NVRAM administratively down down
GigabitEthernet4 unassigned YES NVRAM administratively down down
Loopback0 3.3.3.3 YES manual up up
Loopback1 99.99.99.3 YES manual up up
Tunnel0 200.0.0.1 YES manual up up
Virtual-Access1 200.0.0.1 YES unset up up
Virtual-Template1 200.0.0.1 YES unset up down SPOKE3
SPOKE3#show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet1 100.0.4.1 YES manual up up
GigabitEthernet2 unassigned YES NVRAM administratively down down
GigabitEthernet3 unassigned YES NVRAM administratively down down
GigabitEthernet4 unassigned YES NVRAM administratively down down
Loopback0 4.4.4.4 YES manual up up
Loopback1 99.99.99.4 YES manual up up
Tunnel0 200.0.0.2 YES manual up up
Virtual-Access1 200.0.0.2 YES unset up up
Virtual-Template1 200.0.0.2 YES unset up downshow crypto ikev2 sa
HUB
HUB#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
5 100.0.1.1/500 100.0.2.1/500 UNDERLAY/OVERLAY READY
Encr: AES-GCM, keysize: 256, PRF: SHA512, Hash: None, DH Grp:19, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 300/188 sec
CE id: 0, Session-id: 3
Local spi: 0CCE9DEDD3E6B41A Remote spi: 7EED2DD53D61FF85
Tunnel-id Local Remote fvrf/ivrf Status
7 100.0.1.1/500 100.0.4.1/500 UNDERLAY/OVERLAY READY
Encr: AES-GCM, keysize: 256, PRF: SHA512, Hash: None, DH Grp:19, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 300/8 sec
CE id: 0, Session-id: 2
Local spi: E326D92B178B7236 Remote spi: 9BBF0A43E4EE19DE
Tunnel-id Local Remote fvrf/ivrf Status
6 100.0.1.1/500 100.0.3.1/500 UNDERLAY/OVERLAY READY
Encr: AES-GCM, keysize: 256, PRF: SHA512, Hash: None, DH Grp:19, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 300/69 sec
CE id: 0, Session-id: 1
Local spi: FB8BDE443F82411D Remote spi: DC8BC598F33E3486
IPv6 Crypto IKEv2 SASPOKE1
SPOKE1#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 100.0.2.1/500 100.0.3.1/500 UNDERLAY/OVERLAY READY
Encr: AES-GCM, keysize: 256, PRF: SHA512, Hash: None, DH Grp:19, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 300/195 sec
CE id: 0, Session-id: 2
Local spi: 124F976EA59DBB24 Remote spi: 1BFF979C16A9C7AE
Tunnel-id Local Remote fvrf/ivrf Status
5 100.0.2.1/500 100.0.1.1/500 UNDERLAY/OVERLAY READY
Encr: AES-GCM, keysize: 256, PRF: SHA512, Hash: None, DH Grp:19, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 300/27 sec
CE id: 0, Session-id: 1
Local spi: 4505CB3F49BCB9A2 Remote spi: 956538B32C6EC748
Tunnel-id Local Remote fvrf/ivrf Status
4 100.0.2.1/500 100.0.4.1/500 UNDERLAY/OVERLAY READY
Encr: AES-GCM, keysize: 256, PRF: SHA512, Hash: None, DH Grp:19, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 300/233 sec
CE id: 0, Session-id: 3
Local spi: D6F0FBC2FD5BF843 Remote spi: 631672F84D88B23C
IPv6 Crypto IKEv2 SASPOKE2
SPOKE2#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
5 100.0.3.1/500 100.0.2.1/500 UNDERLAY/OVERLAY READY
Encr: AES-GCM, keysize: 256, PRF: SHA512, Hash: None, DH Grp:19, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 300/2 sec
CE id: 0, Session-id: 2
Local spi: 5AB18E12E7A32F1D Remote spi: 0F4724688F338F93
Tunnel-id Local Remote fvrf/ivrf Status
3 100.0.3.1/500 100.0.1.1/500 UNDERLAY/OVERLAY READY
Encr: AES-GCM, keysize: 256, PRF: SHA512, Hash: None, DH Grp:19, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 300/189 sec
CE id: 0, Session-id: 1
Local spi: DC8BC598F33E3486 Remote spi: FB8BDE443F82411D
IPv6 Crypto IKEv2 SA SPOKE3
SPOKE3#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
5 100.0.4.1/500 100.0.2.1/500 UNDERLAY/OVERLAY READY
Encr: AES-GCM, keysize: 256, PRF: SHA512, Hash: None, DH Grp:19, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 300/89 sec
CE id: 0, Session-id: 2
Local spi: 7CAEE13DB8C2FF4D Remote spi: 2278459FC75A71C9
Tunnel-id Local Remote fvrf/ivrf Status
3 100.0.4.1/500 100.0.1.1/500 UNDERLAY/OVERLAY READY
Encr: AES-GCM, keysize: 256, PRF: SHA512, Hash: None, DH Grp:19, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 300/174 sec
CE id: 0, Session-id: 1
Local spi: 9BBF0A43E4EE19DE Remote spi: E326D92B178B7236
IPv6 Crypto IKEv2 SA show crypto ipsec sa
HUB
HUB#show crypto ipsec sa
interface: Virtual-Access1
Crypto map tag: Virtual-Access1-head-0, local addr 100.0.1.1
protected vrf: OVERLAY
local ident (addr/mask/prot/port): (100.0.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.0.3.1/255.255.255.255/47/0)
current_peer 100.0.3.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 63, #pkts encrypt: 63, #pkts digest: 63
#pkts decaps: 63, #pkts decrypt: 63, #pkts verify: 63
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 100.0.1.1, remote crypto endpt.: 100.0.3.1
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0xA64F6ACD(2790222541)
PFS (Y/N): Y, DH group: group19
inbound esp sas:
spi: 0x51CD2F7E(1372401534)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2043, flow_id: CSR:43, sibling_flags FFFFFFFF80000048, crypto map: Virtual-Access1-head-0, initiator : False
sa timing: remaining key lifetime (k/sec): (4607990/300)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xA64F6ACD(2790222541)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2044, flow_id: CSR:44, sibling_flags FFFFFFFF80000048, crypto map: Virtual-Access1-head-0, initiator : False
sa timing: remaining key lifetime (k/sec): (4607992/300)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
interface: Virtual-Access2
Crypto map tag: Virtual-Access2-head-0, local addr 100.0.1.1
protected vrf: OVERLAY
local ident (addr/mask/prot/port): (100.0.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.0.4.1/255.255.255.255/47/0)
current_peer 100.0.4.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 54, #pkts encrypt: 54, #pkts digest: 54
#pkts decaps: 54, #pkts decrypt: 54, #pkts verify: 54
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 100.0.1.1, remote crypto endpt.: 100.0.4.1
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0xB48F10DF(3029274847)
PFS (Y/N): Y, DH group: group19
inbound esp sas:
spi: 0x3BC00D54(1002442068)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2045, flow_id: CSR:45, sibling_flags FFFFFFFF80000048, crypto map: Virtual-Access2-head-0, initiator : False
sa timing: remaining key lifetime (k/sec): (4607991/388)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xB48F10DF(3029274847)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2046, flow_id: CSR:46, sibling_flags FFFFFFFF80000048, crypto map: Virtual-Access2-head-0, initiator : False
sa timing: remaining key lifetime (k/sec): (4607993/388)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
interface: Virtual-Access3
Crypto map tag: Virtual-Access3-head-0, local addr 100.0.1.1
protected vrf: OVERLAY
local ident (addr/mask/prot/port): (100.0.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.0.2.1/255.255.255.255/47/0)
current_peer 100.0.2.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 50, #pkts encrypt: 50, #pkts digest: 50
#pkts decaps: 50, #pkts decrypt: 50, #pkts verify: 50
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 100.0.1.1, remote crypto endpt.: 100.0.2.1
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0xAA085501(2852672769)
PFS (Y/N): Y, DH group: group19
inbound esp sas:
spi: 0x4C623C8D(1281506445)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2047, flow_id: CSR:47, sibling_flags FFFFFFFF80000048, crypto map: Virtual-Access3-head-0, initiator : False
sa timing: remaining key lifetime (k/sec): (4607992/424)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xAA085501(2852672769)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2048, flow_id: CSR:48, sibling_flags FFFFFFFF80000048, crypto map: Virtual-Access3-head-0, initiator : False
sa timing: remaining key lifetime (k/sec): (4607993/424)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:SPOKE1
SPOKE1#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 100.0.2.1
protected vrf: OVERLAY
local ident (addr/mask/prot/port): (100.0.2.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.0.1.1/255.255.255.255/47/0)
current_peer 100.0.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 641, #pkts encrypt: 641, #pkts digest: 641
#pkts decaps: 645, #pkts decrypt: 645, #pkts verify: 645
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 100.0.2.1, remote crypto endpt.: 100.0.1.1
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0x4C623C8D(1281506445)
PFS (Y/N): Y, DH group: group19
inbound esp sas:
spi: 0xAA085501(2852672769)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2048, flow_id: CSR:48, sibling_flags FFFFFFFF80004048, crypto map: Tunnel0-head-0, initiator : True
sa timing: remaining key lifetime (k/sec): (4607991/369)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x4C623C8D(1281506445)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2047, flow_id: CSR:47, sibling_flags FFFFFFFF80004048, crypto map: Tunnel0-head-0, initiator : True
sa timing: remaining key lifetime (k/sec): (4607993/369)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
interface: Virtual-Access1
Crypto map tag: Virtual-Access1-head-0, local addr 100.0.2.1
protected vrf: OVERLAY
local ident (addr/mask/prot/port): (100.0.2.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.0.3.1/255.255.255.255/47/0)
current_peer 100.0.3.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 651, #pkts encrypt: 651, #pkts digest: 651
#pkts decaps: 649, #pkts decrypt: 649, #pkts verify: 649
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 100.0.2.1, remote crypto endpt.: 100.0.3.1
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0x41B124E4(1102128356)
PFS (Y/N): Y, DH group: group19
inbound esp sas:
spi: 0x39BFAAD8(968862424)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2050, flow_id: CSR:50, sibling_flags FFFFFFFF80004048, crypto map: Virtual-Access1-head-0, initiator : True
sa timing: remaining key lifetime (k/sec): (4607991/440)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x41B124E4(1102128356)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2049, flow_id: CSR:49, sibling_flags FFFFFFFF80004048, crypto map: Virtual-Access1-head-0, initiator : True
sa timing: remaining key lifetime (k/sec): (4607993/440)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
interface: Virtual-Access2
Crypto map tag: Virtual-Access2-head-0, local addr 100.0.2.1
protected vrf: OVERLAY
local ident (addr/mask/prot/port): (100.0.2.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.0.4.1/255.255.255.255/47/0)
current_peer 100.0.4.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 638, #pkts encrypt: 638, #pkts digest: 638
#pkts decaps: 637, #pkts decrypt: 637, #pkts verify: 637
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 100.0.2.1, remote crypto endpt.: 100.0.4.1
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0x2D098C23(755600419)
PFS (Y/N): Y, DH group: group19
inbound esp sas:
spi: 0x7D1FB58C(2099230092)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2052, flow_id: CSR:52, sibling_flags FFFFFFFF80004048, crypto map: Virtual-Access2-head-0, initiator : True
sa timing: remaining key lifetime (k/sec): (4607992/465)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x2D098C23(755600419)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2051, flow_id: CSR:51, sibling_flags FFFFFFFF80004048, crypto map: Virtual-Access2-head-0, initiator : True
sa timing: remaining key lifetime (k/sec): (4607994/465)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:SPOKE2
SPOKE2#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 100.0.3.1
protected vrf: OVERLAY
local ident (addr/mask/prot/port): (100.0.3.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.0.1.1/255.255.255.255/47/0)
current_peer 100.0.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 681, #pkts encrypt: 681, #pkts digest: 681
#pkts decaps: 688, #pkts decrypt: 688, #pkts verify: 688
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 100.0.3.1, remote crypto endpt.: 100.0.1.1
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0x3B34F2D6(993325782)
PFS (Y/N): Y, DH group: group19
inbound esp sas:
spi: 0xFE9B3643(4271584835)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2036, flow_id: CSR:36, sibling_flags FFFFFFFF80004048, crypto map: Tunnel0-head-0, initiator : True
sa timing: remaining key lifetime (k/sec): (4607995/775)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x3B34F2D6(993325782)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2035, flow_id: CSR:35, sibling_flags FFFFFFFF80004048, crypto map: Tunnel0-head-0, initiator : True
sa timing: remaining key lifetime (k/sec): (4607996/775)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
interface: Virtual-Access1
Crypto map tag: Virtual-Access1-head-0, local addr 100.0.3.1
protected vrf: OVERLAY
local ident (addr/mask/prot/port): (100.0.3.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.0.2.1/255.255.255.255/47/0)
current_peer 100.0.2.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 85, #pkts encrypt: 85, #pkts digest: 85
#pkts decaps: 87, #pkts decrypt: 87, #pkts verify: 87
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 100.0.3.1, remote crypto endpt.: 100.0.2.1
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0x39BFAAD8(968862424)
PFS (Y/N): Y, DH group: group19
inbound esp sas:
spi: 0x41B124E4(1102128356)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2033, flow_id: CSR:33, sibling_flags FFFFFFFF80000048, crypto map: Virtual-Access1-head-0, initiator : False
sa timing: remaining key lifetime (k/sec): (4607986/248)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x39BFAAD8(968862424)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2034, flow_id: CSR:34, sibling_flags FFFFFFFF80000048, crypto map: Virtual-Access1-head-0, initiator : False
sa timing: remaining key lifetime (k/sec): (4607989/248)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
interface: Virtual-Access2
Crypto map tag: Virtual-Access2-head-0, local addr 100.0.3.1
protected vrf: OVERLAY
local ident (addr/mask/prot/port): (100.0.3.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.0.4.1/255.255.255.255/47/0)
current_peer 100.0.4.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 18, #pkts encrypt: 18, #pkts digest: 18
#pkts decaps: 17, #pkts decrypt: 17, #pkts verify: 17
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 100.0.3.1, remote crypto endpt.: 100.0.4.1
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0x354849C(55870620)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xC48DF58B(3297637771)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2040, flow_id: CSR:40, sibling_flags FFFFFFFF80004048, crypto map: Virtual-Access2-head-0, initiator : True
sa timing: remaining key lifetime (k/sec): (4607997/849)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x354849C(55870620)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2039, flow_id: CSR:39, sibling_flags FFFFFFFF80004048, crypto map: Virtual-Access2-head-0, initiator : True
sa timing: remaining key lifetime (k/sec): (4607997/849)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:SPOKE3
SPOKE3#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 100.0.4.1
protected vrf: OVERLAY
local ident (addr/mask/prot/port): (100.0.4.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.0.1.1/255.255.255.255/47/0)
current_peer 100.0.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 680, #pkts encrypt: 680, #pkts digest: 680
#pkts decaps: 684, #pkts decrypt: 684, #pkts verify: 684
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 100.0.4.1, remote crypto endpt.: 100.0.1.1
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0x469A99C0(1184537024)
PFS (Y/N): Y, DH group: group19
inbound esp sas:
spi: 0x2BC81807(734533639)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2040, flow_id: CSR:40, sibling_flags FFFFFFFF80004048, crypto map: Tunnel0-head-0, initiator : True
sa timing: remaining key lifetime (k/sec): (4607997/763)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x469A99C0(1184537024)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2039, flow_id: CSR:39, sibling_flags FFFFFFFF80004048, crypto map: Tunnel0-head-0, initiator : True
sa timing: remaining key lifetime (k/sec): (4607998/763)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
interface: Virtual-Access1
Crypto map tag: Virtual-Access1-head-0, local addr 100.0.4.1
protected vrf: OVERLAY
local ident (addr/mask/prot/port): (100.0.4.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.0.2.1/255.255.255.255/47/0)
current_peer 100.0.2.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 1, #pkts encrypt: 1, #pkts digest: 1
#pkts decaps: 1, #pkts decrypt: 1, #pkts verify: 1
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 100.0.4.1, remote crypto endpt.: 100.0.2.1
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0x89CF9F11(2312085265)
PFS (Y/N): Y, DH group: group19
inbound esp sas:
spi: 0xBCA7EEC4(3165122244)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2041, flow_id: CSR:41, sibling_flags FFFFFFFF80000048, crypto map: Virtual-Access1-head-0, initiator : False
sa timing: remaining key lifetime (k/sec): (4607999/886)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x89CF9F11(2312085265)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2042, flow_id: CSR:42, sibling_flags FFFFFFFF80000048, crypto map: Virtual-Access1-head-0, initiator : False
sa timing: remaining key lifetime (k/sec): (4607999/886)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
interface: Virtual-Access2
Crypto map tag: Virtual-Access2-head-0, local addr 100.0.4.1
protected vrf: OVERLAY
local ident (addr/mask/prot/port): (100.0.4.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (100.0.3.1/255.255.255.255/47/0)
current_peer 100.0.3.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 32, #pkts encrypt: 32, #pkts digest: 32
#pkts decaps: 31, #pkts decrypt: 31, #pkts verify: 31
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 100.0.4.1, remote crypto endpt.: 100.0.3.1
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0xC48DF58B(3297637771)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x354849C(55870620)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2035, flow_id: CSR:35, sibling_flags FFFFFFFF80000048, crypto map: Virtual-Access2-head-0, initiator : False
sa timing: remaining key lifetime (k/sec): (4607995/734)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xC48DF58B(3297637771)
transform: esp-gcm ,
in use settings ={Tunnel, }
conn id: 2036, flow_id: CSR:36, sibling_flags FFFFFFFF80000048, crypto map: Virtual-Access2-head-0, initiator : False
sa timing: remaining key lifetime (k/sec): (4607996/734)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:show ip ospf neighbor
HUB
HUB# show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
2.2.2.2 0 FULL/ - 00:00:39 200.0.0.3 Virtual-Access3
4.4.4.4 0 FULL/ - 00:00:31 200.0.0.2 Virtual-Access2
3.3.3.3 0 FULL/ - 00:00:38 200.0.0.1 Virtual-Access1SPOKE1
SPOKE1#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
4.4.4.4 0 FULL/ - 00:00:31 200.0.0.2 Virtual-Access2
3.3.3.3 0 FULL/ - 00:00:39 200.0.0.1 Virtual-Access1
1.1.1.1 0 FULL/ - 00:00:37 200.0.0.254 Tunnel0SPOKE2
SPOKE2#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
4.4.4.4 0 FULL/ - 00:00:33 200.0.0.2 Virtual-Access2
2.2.2.2 0 FULL/ - 00:00:30 200.0.0.3 Virtual-Access1
1.1.1.1 0 FULL/ - 00:00:32 200.0.0.254 Tunnel0SPOKE3
SPOKE3#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
3.3.3.3 0 FULL/ - 00:00:34 200.0.0.1 Virtual-Access2
2.2.2.2 0 FULL/ - 00:00:39 200.0.0.3 Virtual-Access1
1.1.1.1 0 FULL/ - 00:00:31 200.0.0.254 Tunnel0show ip route vrf UNDERLAY
HUB
HUB#show ip route vrf UNDERLAY
Routing Table: UNDERLAY
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is not set
1.0.0.0/32 is subnetted, 1 subnets
C 1.1.1.1 is directly connected, Loopback0
2.0.0.0/32 is subnetted, 1 subnets
i L1 2.2.2.2 [115/30] via 100.0.1.254, 01:44:15, GigabitEthernet1
3.0.0.0/32 is subnetted, 1 subnets
i L1 3.3.3.3 [115/30] via 100.0.1.254, 02:24:11, GigabitEthernet1
4.0.0.0/32 is subnetted, 1 subnets
i L1 4.4.4.4 [115/30] via 100.0.1.254, 02:23:44, GigabitEthernet1
50.0.0.0/32 is subnetted, 1 subnets
i L1 50.50.50.50 [115/20] via 100.0.1.254, 02:25:08, GigabitEthernet1
100.0.0.0/8 is variably subnetted, 5 subnets, 2 masks
C 100.0.1.0/24 is directly connected, GigabitEthernet1
L 100.0.1.1/32 is directly connected, GigabitEthernet1
i L1 100.0.2.0/24 [115/20] via 100.0.1.254, 02:25:08, GigabitEthernet1
i L1 100.0.3.0/24 [115/20] via 100.0.1.254, 02:25:08, GigabitEthernet1
i L1 100.0.4.0/24 [115/20] via 100.0.1.254, 02:25:08, GigabitEthernet1SPOKE1
SPOKE1#show ip route vrf UNDERLAY
Routing Table: UNDERLAY
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is not set
1.0.0.0/32 is subnetted, 1 subnets
i L1 1.1.1.1 [115/30] via 100.0.2.254, 01:44:44, GigabitEthernet1
2.0.0.0/32 is subnetted, 1 subnets
C 2.2.2.2 is directly connected, Loopback0
3.0.0.0/32 is subnetted, 1 subnets
i L1 3.3.3.3 [115/30] via 100.0.2.254, 01:44:44, GigabitEthernet1
4.0.0.0/32 is subnetted, 1 subnets
i L1 4.4.4.4 [115/30] via 100.0.2.254, 01:44:44, GigabitEthernet1
50.0.0.0/32 is subnetted, 1 subnets
i L1 50.50.50.50 [115/20] via 100.0.2.254, 01:44:47, GigabitEthernet1
100.0.0.0/8 is variably subnetted, 5 subnets, 2 masks
i L1 100.0.1.0/24 [115/20] via 100.0.2.254, 01:44:47, GigabitEthernet1
C 100.0.2.0/24 is directly connected, GigabitEthernet1
L 100.0.2.1/32 is directly connected, GigabitEthernet1
i L1 100.0.3.0/24 [115/20] via 100.0.2.254, 01:44:47, GigabitEthernet1
i L1 100.0.4.0/24 [115/20] via 100.0.2.254, 01:44:47, GigabitEthernet1SPOKE2
SPOKE2#show ip route vrf UNDERLAY
Routing Table: UNDERLAY
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is not set
1.0.0.0/32 is subnetted, 1 subnets
i L1 1.1.1.1 [115/30] via 100.0.3.254, 01:47:48, GigabitEthernet1
2.0.0.0/32 is subnetted, 1 subnets
i L1 2.2.2.2 [115/30] via 100.0.3.254, 01:44:51, GigabitEthernet1
3.0.0.0/32 is subnetted, 1 subnets
C 3.3.3.3 is directly connected, Loopback0
4.0.0.0/32 is subnetted, 1 subnets
i L1 4.4.4.4 [115/30] via 100.0.3.254, 02:24:19, GigabitEthernet1
50.0.0.0/32 is subnetted, 1 subnets
i L1 50.50.50.50 [115/20] via 100.0.3.254, 02:24:47, GigabitEthernet1
100.0.0.0/8 is variably subnetted, 5 subnets, 2 masks
i L1 100.0.1.0/24 [115/20] via 100.0.3.254, 02:24:47, GigabitEthernet1
i L1 100.0.2.0/24 [115/20] via 100.0.3.254, 02:24:47, GigabitEthernet1
C 100.0.3.0/24 is directly connected, GigabitEthernet1
L 100.0.3.1/32 is directly connected, GigabitEthernet1
i L1 100.0.4.0/24 [115/20] via 100.0.3.254, 02:24:47, GigabitEthernet1SPOKE3
SPOKE3#show ip route vrf UNDERLAY
Routing Table: UNDERLAY
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is not set
1.0.0.0/32 is subnetted, 1 subnets
i L1 1.1.1.1 [115/30] via 100.0.4.254, 01:47:53, GigabitEthernet1
2.0.0.0/32 is subnetted, 1 subnets
i L1 2.2.2.2 [115/30] via 100.0.4.254, 01:44:55, GigabitEthernet1
3.0.0.0/32 is subnetted, 1 subnets
i L1 3.3.3.3 [115/30] via 100.0.4.254, 02:24:19, GigabitEthernet1
4.0.0.0/32 is subnetted, 1 subnets
C 4.4.4.4 is directly connected, Loopback0
50.0.0.0/32 is subnetted, 1 subnets
i L1 50.50.50.50 [115/20] via 100.0.4.254, 02:24:24, GigabitEthernet1
100.0.0.0/8 is variably subnetted, 5 subnets, 2 masks
i L1 100.0.1.0/24 [115/20] via 100.0.4.254, 02:24:24, GigabitEthernet1
i L1 100.0.2.0/24 [115/20] via 100.0.4.254, 02:24:24, GigabitEthernet1
i L1 100.0.3.0/24 [115/20] via 100.0.4.254, 02:24:24, GigabitEthernet1
C 100.0.4.0/24 is directly connected, GigabitEthernet1
L 100.0.4.1/32 is directly connected, GigabitEthernet1show ip route vrf OVERLAY
HUB
HUB#show ip route vrf OVERLAY
Routing Table: OVERLAY
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is not set
99.0.0.0/32 is subnetted, 4 subnets
C 99.99.99.1 is directly connected, Loopback1
O 99.99.99.2 [110/1001] via 200.0.0.3, 01:45:40, Virtual-Access3
O 99.99.99.3 [110/1001] via 200.0.0.1, 01:47:53, Virtual-Access1
O 99.99.99.4 [110/1001] via 200.0.0.2, 01:46:23, Virtual-Access2
200.0.0.0/32 is subnetted, 4 subnets
S 200.0.0.1 is directly connected, Virtual-Access1
S 200.0.0.2 is directly connected, Virtual-Access2
S 200.0.0.3 is directly connected, Virtual-Access3
C 200.0.0.254 is directly connected, Loopback2SPOKE1
SPOKE1#show ip route vrf OVERLAY
Routing Table: OVERLAY
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is not set
99.0.0.0/32 is subnetted, 4 subnets
O 99.99.99.1 [110/1001] via 200.0.0.254, 01:46:11, Tunnel0
C 99.99.99.2 is directly connected, Loopback1
O 99.99.99.3 [110/1001] via 200.0.0.1, 01:45:02, Virtual-Access1
O 99.99.99.4 [110/1001] via 200.0.0.2, 01:45:08, Virtual-Access2
200.0.0.0/32 is subnetted, 4 subnets
S % 200.0.0.1 is directly connected, Virtual-Access1
S % 200.0.0.2 is directly connected, Virtual-Access2
C 200.0.0.3 is directly connected, Tunnel0
S 200.0.0.254 is directly connected, Tunnel0SPOKE2
SPOKE2#show ip route vrf OVERLAY
Routing Table: OVERLAY
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is not set
99.0.0.0/32 is subnetted, 4 subnets
O 99.99.99.1 [110/1001] via 200.0.0.254, 01:48:34, Tunnel0
O 99.99.99.2 [110/1001] via 200.0.0.3, 01:45:13, Virtual-Access1
C 99.99.99.3 is directly connected, Loopback1
O 99.99.99.4 [110/1001] via 200.0.0.2, 00:08:33, Virtual-Access2
200.0.0.0/32 is subnetted, 4 subnets
C 200.0.0.1 is directly connected, Tunnel0
S % 200.0.0.2 is directly connected, Virtual-Access2
S % 200.0.0.3 is directly connected, Virtual-Access1
S 200.0.0.254 is directly connected, Tunnel0SPOKE3
SPOKE3#show ip route vrf OVERLAY
Routing Table: OVERLAY
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is not set
99.0.0.0/32 is subnetted, 4 subnets
O 99.99.99.1 [110/1001] via 200.0.0.254, 01:47:21, Tunnel0
O 99.99.99.2 [110/1001] via 200.0.0.3, 01:45:36, Virtual-Access1
O 99.99.99.3 [110/1001] via 200.0.0.1, 00:08:49, Virtual-Access2
C 99.99.99.4 is directly connected, Loopback1
200.0.0.0/32 is subnetted, 4 subnets
S % 200.0.0.1 is directly connected, Virtual-Access2
C 200.0.0.2 is directly connected, Tunnel0
S % 200.0.0.3 is directly connected, Virtual-Access1
S 200.0.0.254 is directly connected, Tunnel0疎通確認
スポーク間の通信がハブ経由ではなく、ショートカットVPNで直接通信できているかを確認します。
traceroute vrf OVERLAY ~
SPOKE1
SPOKE1#traceroute vrf OVERLAY 99.99.99.3
Type escape sequence to abort.
Tracing the route to 99.99.99.3
VRF info: (vrf in name/id, vrf out name/id)
1 200.0.0.1 5 msec 2 msec *
SPOKE1#traceroute vrf OVERLAY 99.99.99.4
Type escape sequence to abort.
Tracing the route to 99.99.99.4
VRF info: (vrf in name/id, vrf out name/id)
1 200.0.0.2 1 msec 2 msec * SPOKE2
SPOKE2#traceroute vrf OVERLAY 99.99.99.2
Type escape sequence to abort.
Tracing the route to 99.99.99.2
VRF info: (vrf in name/id, vrf out name/id)
1 200.0.0.3 9 msec 1 msec *
SPOKE2#traceroute vrf OVERLAY 99.99.99.4
Type escape sequence to abort.
Tracing the route to 99.99.99.4
VRF info: (vrf in name/id, vrf out name/id)
1 200.0.0.2 2 msec 3 msec * SPOKE3
SPOKE3#traceroute vrf OVERLAY 99.99.99.2
Type escape sequence to abort.
Tracing the route to 99.99.99.2
VRF info: (vrf in name/id, vrf out name/id)
1 200.0.0.3 5 msec 3 msec *
SPOKE3#traceroute vrf OVERLAY 99.99.99.3
Type escape sequence to abort.
Tracing the route to 99.99.99.3
VRF info: (vrf in name/id, vrf out name/id)
1 200.0.0.1 3 msec 2 msec * 1HopなのでショートカットVPNを使っていそうです。
後書き
「show crypto ipsec sa」のいくつかのトンネルが「PFS (Y/N): N, DH group: none」になっており、PFSが機能していないように見えますが、これは初回のIPsec SA構築時にはPSFが利用されないのが理由のようです。IPsec SAの張り直しが実行されると「PFS (Y/N): Y, DH group: group19」になります。
そのためにIPsec SAのライフサイクルを最短である900に設定していましたが、このブログを書いたときは、いくつかのショートカットVPNをそもそも起動させていなかった(pingなどで通信が発生するとショートカットVPNを張りに行く)ので、このログ結果になってます。
IPsecと真剣に向き合ったのは初めてなので結構躓いたりしましたが、何とか形になったので稚拙を礎により良いネットワークが生まれることを切に願います🙄

コメント